Kaspersky's Global Research and Analysis Team (GReAT) has uncovered the emergence of three cross-platform threats and reveals three new strategies being employed by cybercriminals using the FakeSG campaign, Akira ransomware, and AMOS macOS stealer in its latest report.
The contemporary crimeware landscape is marked by constant evolution, as cybercriminals deploy sophisticated tactics across various platforms to exploit victims. Kaspersky experts analyse various threats, including cross-platform ransomware, macOS stealers, and malware distribution campaigns.
The latest cyber threat uncovered by GReAT is FakeSG, where legitimate websites are compromised to display deceptive browser update notifications. Clicking on these notifications triggers the download of a harmful file, and despite changing URLs, the path (/cdn/wds.min.php) remains constant. The downloaded file runs hidden scripts, prompting users to update their browsers, while establishing persistence through scheduled tasks. Within the archive, a malicious configuration file exposes the Command and Control (C2) address, highlighting the sophistication of this campaign.
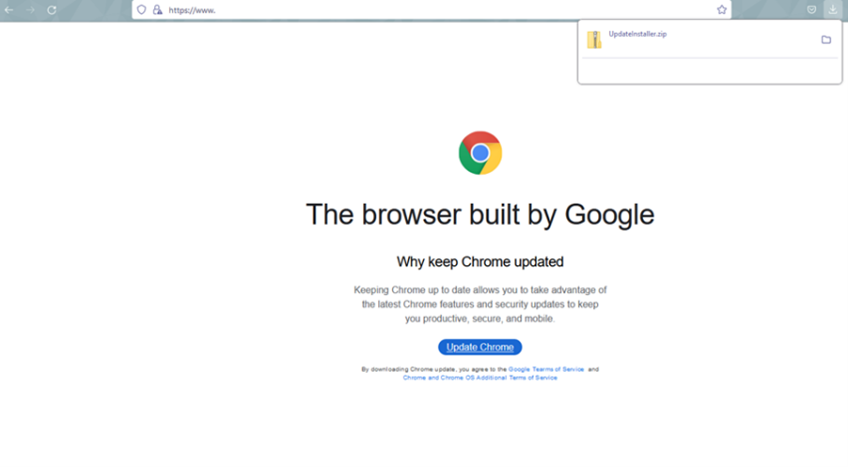
Example of landing page
Akira, a new ransomware variant affecting both Windows and Linux systems, has swiftly infected more than 60 organisations globally, targeting retail, consumer goods, and education establishments. Its adaptability to work across platforms emphasises the broad impact on diverse industries. Sharing traits with Conti, such as an identical folder exclusion list, Akira features a distinctive Command and Control (C2) panel with an old-school minimalistic design, fortifying against analysis attempts. This highlights the evolving sophistication of cyber threats.
The AMOS macOS stealer, surfacing in April 2023, and initially sold for US$1,000/month on Telegram, and evolved from Go to C, deploying malvertising on cloned software sites. Also using deceptive methods like malvertising, it infiltrates macOS systems, retrieving and compressing user data for transmission to the Command and Control server, utilising a unique UUID for identification. This reflects a growing trend of macOS-specific stealers exploiting potential vulnerabilities, deviating from their traditional association with Windows platforms.
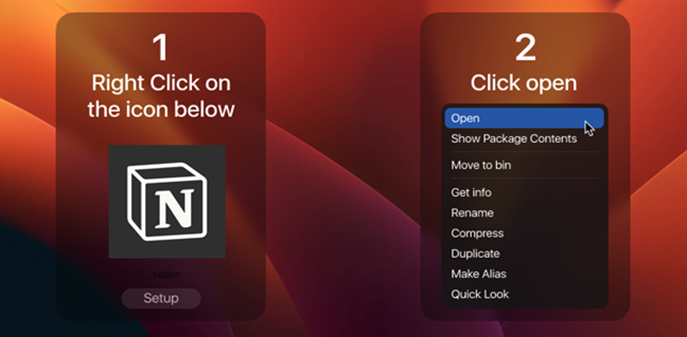
Malware installation instructions
“Adapting to the dynamic landscape of cyber threats is paramount to safeguarding our digital environments. The emergence of this new crimeware, coupled with the non-standard methods cybercriminals employ across diverse operating systems, underscores the urgency for vigilance and innovation in detection. Staying one step ahead requires a collective effort, emphasising the crucial role of continuous research and collaboration to fortify our defenses against evolving cyber threats,” comments Jornt van der Wiel, senior security researcher at GReAT.
To read the full report, please visit Securelist.com.















